HTTP Basic Authentication brief explanation
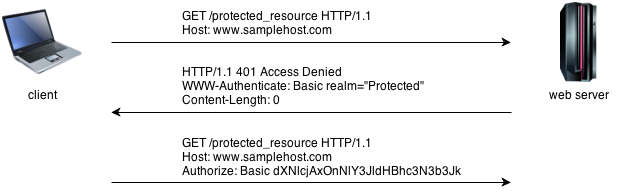
HTTP supports several authentication mechanisms. Upon a request for resource within a protected space the server should respond with authentication challenge using WWW-Authenticate header. In order to receive authorization the client should send requested identification information using Authorization header. When the client is not authorised a 401 “Unauthorised” response status is returned.
There are several authentication schemes supported: Basic, Digest, Negotiate, Kerberos, NTLM, OAuth.
The simplest and most common HTTP authentication in use is Basic. The clients need to provide the credentials in a Base64 encoded string username:password. If the credentials are correct the web server returns the requested resource otherwise the server repeats the authentication challenge.
The diagram below depicts sample communication between the parties. (The Base64 encoded string corresponds to user01:secretpassword plain string)
Security implications
Obviously if HTTPS is not implemented the credentials are passed from the client to the server in clear text across the network and because of that are subject of man in the middle attacks.
Due to the HTTP stateless nature the client needs to provide the same information each time a resource within the protected realm is requested. Obviously this provides the attacker with a large window. Usually the browser caches the password for the time of the session in order to make the interaction human friendly and that could pose a threat in case of attacks targeting the client browser itself.
And finally the basic HTTP authentication is extremely succeptable to brute-force attacks.
Implementing HTTP authentication dictionary/brute-force attack
Unless you fancy scripting your own tool to automate the brute-force attack you would probably go for something that is already there.
Hydra and Brutus are able to implement basic HTTP authentication dictionary attacks. For those you will need a list of usernames and list of passwords to pass to the tools.
BurpSuite however is my tool of choice for most of my web testing and I’m using it for dictionary and brute force attacks against HTTP Basic authentication as well. Both Burp Suite Free Edition and Burp Suite Professional are suitable for the purpose.
Burp Suite against HTTP Basic authentication
There are probably several options to go with the bruteforcing task using Burp Suite but here is my approach.
Send the authentication request to the Intruder
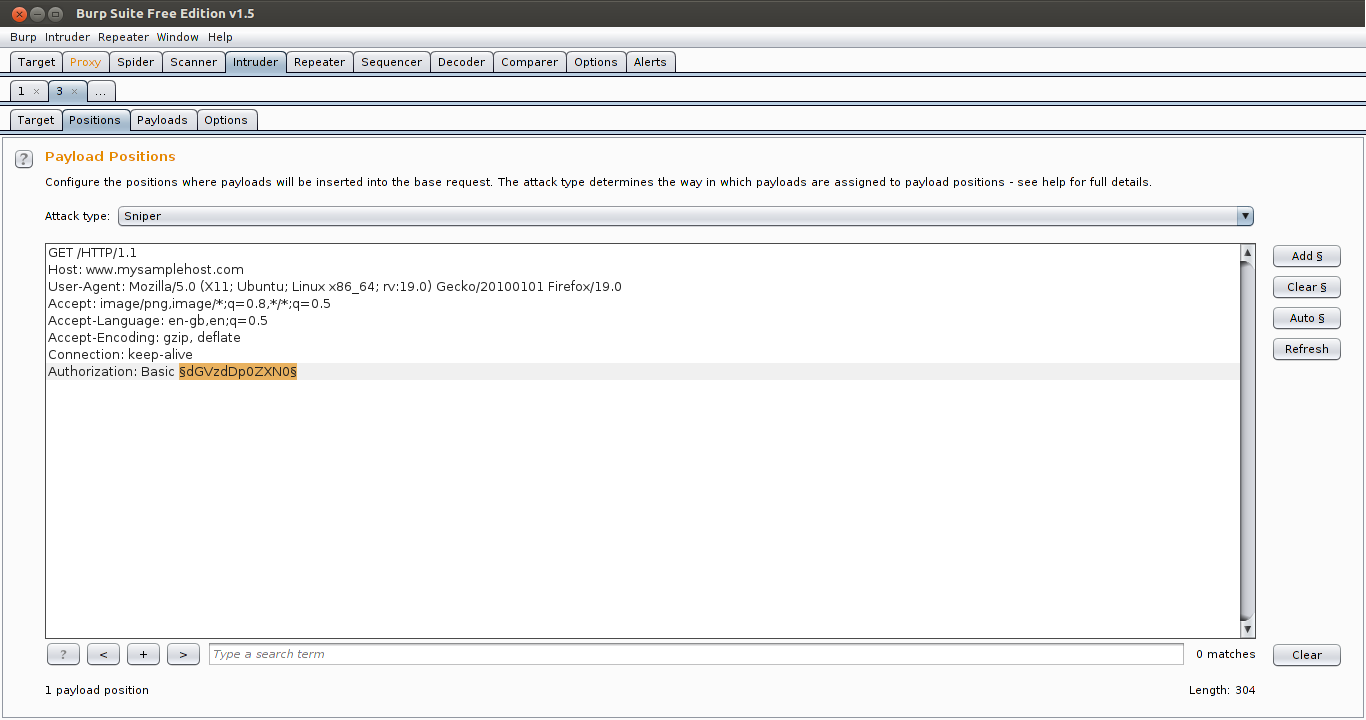
To implement the attack you need to capture one authentication request with Burp Proxy and send it to Burp Intruder.
Remove all the variable marking that Burp automatically places here and there by clicking Clear button. Mark only the Base64 encoded string and click Add button to put the markers around it.
Now you need to specify the payload.
I’m using different payload types for dictionary and brute-force attacks.
Dictionary attack
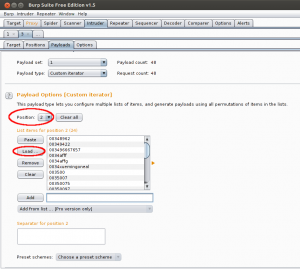
For the dictionary attack I’m using custom iterator intruder option. It allows you to generate your own custom payload string consisting from several substrings. For every substring you could specify separator which is basically e suffix. The Intruder calls those substrings “positions”.
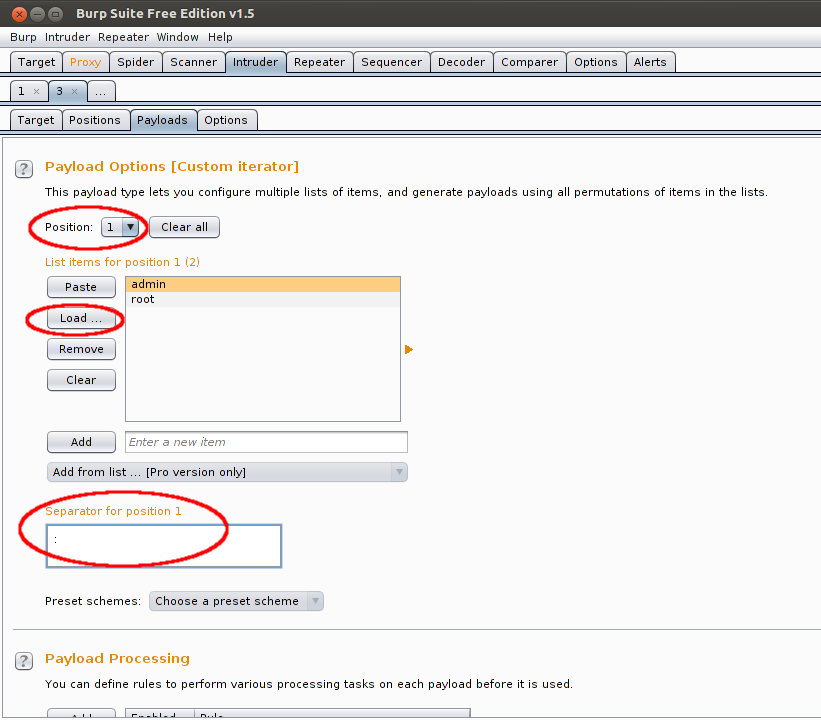
Following this logic in position 1 we would like to load an username followed by separator semicolumn and then load password for position 2.
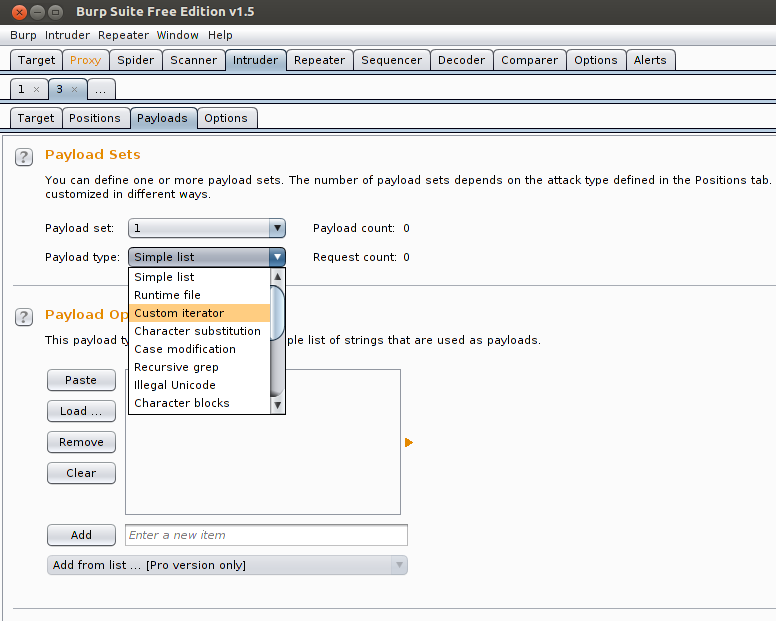
Go to Payload tab and select Custom iterator option from Payload type dropdown box.
Select position 1 from the Position dropdown box and load your usernames list in List items for position 1 listbox. Put semicolumn in the Separator for position 1 text box.
Select position 2 from the Position dropdown box and load your passwords list in List items for position 2 listbox.
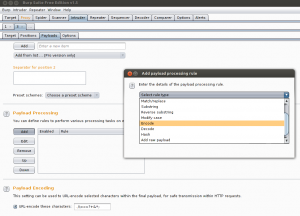
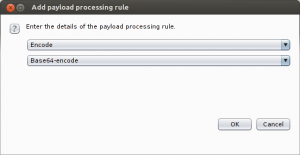
After you’ve set your two positions you need to tell the Intruder to encode the payload string using Base64 encoding. Go to Payload processing sections and click Add button. Select Payload encoding option and then Base64.
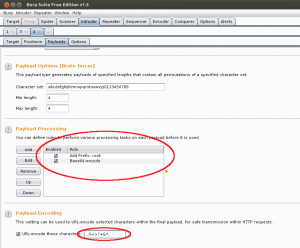
By default Burp Intruder URL encodes the payload. Base64 strings often contain = symbol. That is why it is a good idea to exclude it from the list of URL characters for encoding.
That’s it. You can start the Intruder attack.
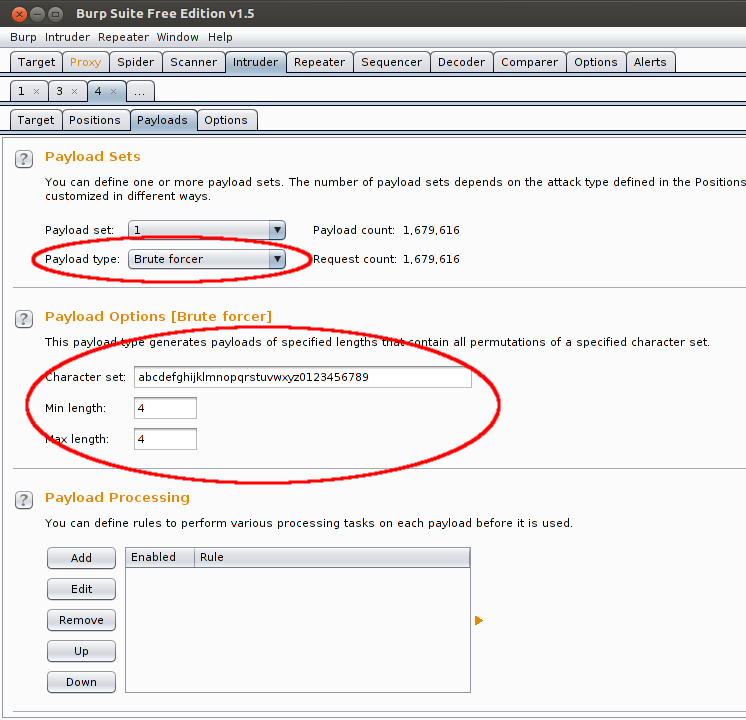
Bruteforce attack
The method I’m using for the bruteforce attack is targeting only one username per Intruder attack.
Select Brute forcer from the Payload type dropdown and then set the length of the password and the characterset you would like the Intruder to use while constructing the password strings.
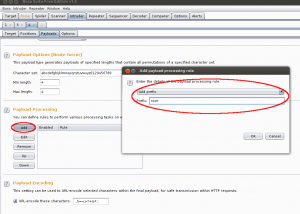
In order to specify the username you would like to brute-force you need to set Payload processing rule. Add new rule with Add prefix type and fill up the username followed by semi-column.
Add another rule to encode the payload using Base64. And finally remove = from the list of symbols subject of URL encoding.
Done! You can start the Intruder attack!
Happy bruteforcing!
NOTES: Burp Suite Free Edition and Burp Suite Professional are developed and licensed by PortSwigger Ltd





Leave a Reply